We are a Full-Service Vacation Rental Marketing Agency. We help your business increase profits and brand awareness. We analyze your business, built a marketing plan, implement it and measure success.
Analytics and Consulting
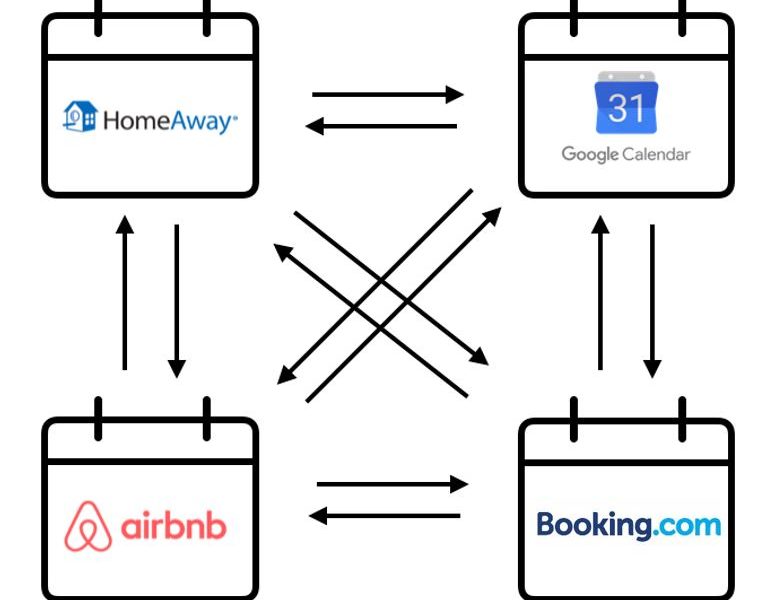
Social Media and Web Development
Content Marketing
Marketing Strategy
SEO & Ranking
Contact us
+34.654.915.163
admin@rentalsmarketing.com
Calle Doctor Trueta 113, Barcelona, Spain